Thread 中讨论的其他器件: Z-stack
尊敬的 Ryan Brown1和 YK:
很长时间了、很抱歉中断、我们在 CC2530的 Z-stack 3.0.2上遇到了一个奇怪的行为、这导致我们的器件(ZR)丢失 ZigBee 网络(看起来像是离开、但没有收到任何离开请求) 在下一个下电上电周期中、众所周知、z-stack 3.0.2一直非常稳定 、直到现在、即使没有更新、也至少有3年以上的时间、因此我们不认为堆栈有一些缺陷。
因此、我们 必须研究 BDB 规格文档才能找到一些事实。 ZigBee Alliance 的 BDB 规范
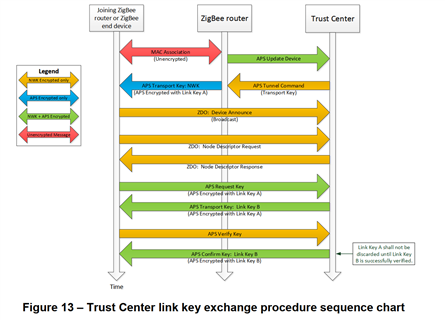
"10.2.6接收新的链路密钥" BDB 文档表格描述了如果节点接收 到传输密钥包含 TCLK 但尚未发送请求密钥时的行为、它应忽略该消息以及变量 acceptNewUnrequestedTrustCenterLinkKey
看起来就像在 ZDSecMgr.c 源文件中找到的、但 它是注释、因此我们不知道 z-stack 中的行为。
附件是我们的 OTA 捕获、ubiqua、0xE46C 和0xA1D7会在下一个下电上电周期中丢失 ZigBee 网络信息。
非常感谢。
e2e.ti.com/.../0xE46C-and-0xA1D7-loss-network-information.zip