28377d用的确实很爽,可是这DCSM要把人搞疯。
加密已经搞了几天,锁是锁上了,但是把GRABSECTR,GRABRAMR,EXEONLYSECTR,EXEONLYRAMR四个寄存器都烧成0,程序就不跑了,重新传程序,重新上电也不行。OTP也改不了,一旦锁上,就是UNLOCK了,JTAG也是啥也看不成,锁上之后程序不跑也不知是何原因。因为OTP,前后已经搞废2片了。28377D这OTP让人好无奈啊。崩溃中T_T
This thread has been locked.
If you have a related question, please click the "Ask a related question" button in the top right corner. The newly created question will be automatically linked to this question.
28377d用的确实很爽,可是这DCSM要把人搞疯。
加密已经搞了几天,锁是锁上了,但是把GRABSECTR,GRABRAMR,EXEONLYSECTR,EXEONLYRAMR四个寄存器都烧成0,程序就不跑了,重新传程序,重新上电也不行。OTP也改不了,一旦锁上,就是UNLOCK了,JTAG也是啥也看不成,锁上之后程序不跑也不知是何原因。因为OTP,前后已经搞废2片了。28377D这OTP让人好无奈啊。崩溃中T_T
technical reference guide我是一字不落,看好几遍。
首先这两个寄存器GRABSECTR GRABRAMR不配置的话,4个CSMKEY即便是LOCK也没有用,按照手册上说的,这两个寄存器配置如下。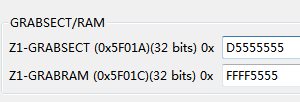
配置完直接出现JTAG无法连接目标板的情况。
目标板供电没有问题,没有虚焊,连不上仿真器但是程序运行正常。板卡功耗正常,和未加密之前无差别。测试烧写2块目标板,出现的情况一致。
Console输出如下:
C28xx_CPU1: Trouble Halting Target CPU: (Error -1156 @ 0x0) Device may be operating in low-power mode. Do you want to bring it out of this mode? Choose 'Yes' to force the device to wake up and retry the operation. Choose 'No' to retry the operation without waking the device. (Emulation package 6.0.628.1) C28xx_CPU1: Error: (Error -2134 @ 0x0) Unable to control device execution state. Reset the device, and retry the operation. If error persists, confirm configuration, power-cycle the board, and/or try more reliable JTAG settings (e.g. lower TCLK). (Emulation package 6.0.628.1) C28xx_CPU1: Error: (Error -1135 @ 0x0) The debug probe reported an error. Confirm debug probe configuration and connections, reset the debug probe, and retry the operation. (Emulation package 6.0.628.1) C28xx_CPU1: Unable to determine target status after 20 attempts C28xx_CPU1: Failed to remove the debug state from the target before disconnecting. There may still be breakpoint op-codes embedded in program memory. It is recommended that you reset the emulator before you connect and reload your program before you continue debugging C28xx_CPU1: GEL: Error while executing OnTargetConnect(): Could not write 0x0005F412@Data: target is not connected at *((int *) 0x5F412)=0x000F [f28377d_cpu1.gel:80] at OnTargetConnect()
既然GRABSECTR GRABRAMR寄存器各位烧写0x01不行,干脆都烧成0x00。继续换板子,两个寄存器都烧写0x00000000。还是连不上仿真器。
既然GRAB寄存器搞不定,我测试EXEONLYSECT EXEONLYRAM 这两个寄存器。继续换板子,两个寄存器都烧写0x00000000。烧写后程序不运行。观察板卡功耗,和没有烧写程序的功耗一样。认为是没有BOOT成功或者INIT_FLASH未成功。BOOTMODE两个引脚均上拉,寄存器默认配置。FLASHBOOT无误。
查手册有提示。
2.13.1.3 Execute-Only Protection To achieve a higher level of security on secure Flash sectors and RAM blocks that store critical user code (instruction opcodes), the Execute-Only protection feature is provided. When the Execute-Only protection is turned on for any secure Flash sector or RAM block, data reads to that Flash sectors are disallowed from any code (even from secure code). Execute-only protection for a Flash sector and RAM block can be turned on by configuring the bit field associated for that particular sector/RAM block in the zone's (which has ownership of that sector/RAM block) EXEONLYSECT and EXEONLYRAM register, respectively
3.27.1 Safe Copy Code Functions (Z1 and Z2) To allow code copy from a secure, EXEONLY flash sector to a secure, EXEONLY RAM belonging to the same zone, dedicated TI-provided code copy functions, which are programmed in secure ROM, should be used. These functions are denoted as SafeCopyCodeZ1() (for zone1) and SafeCopyCodeZ2() (for zone2) and are supported by hardware to allow users to copy the data from secure, EXEONLY flash sectors, to secure, EXEONLY RAM without compromising security. The application must ensure that the interrupts are disabled before calling the SafeCopyCodeZx() functions. The device will reset if an interrupt or NMI vector is fetched during execution of these functions. The following is an example of how the copy function is used: STEC INTM Status = SafeCopyCodeZx(size,(Uint16 *)dest, (Uint16 *)src); CLRC INTM Prototypes: Uint16 SafeCopycodeZ1(Uint32 size, Uint16 *dst, Uint16 *src); Uint16 SafeCopycodeZ2(Uint32 size, Uint16 *dst, Uint16 *src); src – Source address in flash which is secure and EXEONLY enabled. dst – Destination address in RAM which is secure, EXEONLY enabled and in same zone as source flash. size – Number of words(16bit) to be copied. The function returns the number of words copied. The application must ensure that the source flash sector and destination RAM block belongs to the same zone, and variables src, src+size should fall within a sector boundary and dst, dst+size should fall within a RAM block boundary. If any one of these conditions fails, function will return zero.
添加库,使用SafeCopyCodeZ1((size_t)&RamfuncsLoadSize, &RamfuncsRunStart, &RamfuncsLoadStart);转移的FLASH和RAM都是EXEONLY使能过了,可无论如何修改程序和CMD,板卡状态没有丝毫的改变。
折腾了几天,打样的7块板子全部都烧的半死不活。现在已经不知从何下手,累觉不爱。
2.13.1
There are three types of accesses: data/program reads, JTAG access, and instruction fetches (calls,
jumps, code executions, ISRs). Instruction fetches are never blocked. JTAG accesses are always blocked
when a memory is secure. Data reads to a secure memory are always blocked unless the program is
executing from a memory which belongs to the same zone. Data reads to unsecure memory are always
allowed. Table 2-15 shows the levels of security.
0x5F412是MEM_CFG_REGS Registers 的DxINIT Register初始化RAM,M0,M1,D0,D1。虽然GRAB寄存器阻塞了JTAG对M0,M1,D0,D1的访问,但是并没有阻塞这个DxINIT Register的访问。而且GRAB寄存器永远不阻塞指令。写DxINIT Register和JTAG没关系吧。但是console提示Could not write 0x0005F412@Data
是否GRAB寄存器会阻塞通过JTAG访问RAM以外的一些寄存器对的RAM的访问。如果是这样,unlock才能连上JTAG,但是连不上JTAG,unlock不了啊。矛盾啊
已解决。
但不知为何GRABRAM和GRABSECT寄存器任意域一旦烧录为非11数据,连接JTAG必须要按着复位按钮,连上后再松开才可以。
中间遇到的一些问题写下和大家分享。先看这个图。
ZX-LINKPOINTER三个数据对应的是DCSM相关OTP寄存器的存储位置偏移。LINKPOINTER1,LINKPOINTER2,LINKPOINTER3,三个寄存器没有ECC校验(除此外DCSM寄存器均有ECC校验),这三个寄存器的的值必须一样!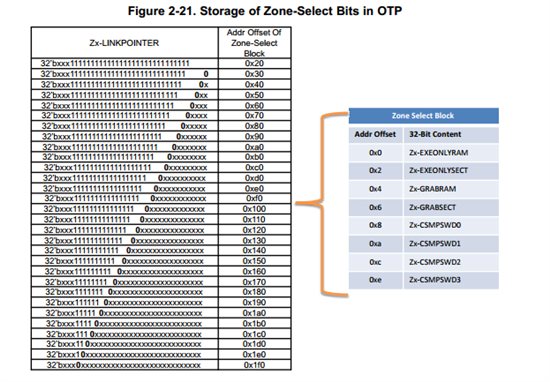
再看这个图,LINKPOINTER存贮的值对应的是CSMPSWD,GRAB,EXEONLY相关寄存器的首地址偏移值。0XFFFFFFFF对应偏移值为0x20,即0x78020为以上几个寄存器的首地址。这么做的好处是OTP一旦从1烧成0就改不了了,如果烧错,还可以修改LINKPOINTER的值,重新换一个区烧写。但是只有32次机会。建议烧写LINKPOINTER的时候,从0xFFFFFFFF开始。能多烧几次- -!
其次看PSWDLOCK,CRCLOCK,BOOTCTRL寄存器,这三个寄存器不在LINKPOINTER区之内,烧写只有一次机会,相关域烧成零就改不了了。
PSWDLOCK作用是CSMPSWD密码锁定之后不能从JTAG或者MEMORY BROWSER读取。
CRCLOCK,BOOTCTRL没什么歧义,自己看手册。
再说CSMPSWD,一共四个32位寄存器,对应4组密码。烧录密码后,断电重新上电会自行LOCK。但是和以往芯片不同,这没什么卵用。LOCK之后,RAM,FLASH的数据仍然可以从JTAG或者MEMORY读出。需要配合GRAB或者EXEONLY寄存器使用才可以。
GRAB有GRABRAM和GRABSECT两个寄存器,对应RAM和FLASH分配给Z1或者Z2区,相关域设置为0x11时,RAM和FLASH都不安全。都可读取。相关对应关系如下图
FLASH同理。但是这里实验发现相关域设置成0x01或者0x10,unlock对应区域后,RAM和FLASH通过JTAG或者MEMORY看仍然全是0。意思就是,我把芯片锁上了,你别想破解,当然我自己也打不开- -!想要重新传程序,要修改linkpointer的值,当然次数也是有限的。
EXEONLY暂时先不说了,加密性更好,自己去琢磨吧,用这个寄存器之后,需要修改代码,添加F2837xRevB_c1rom_SafeZoneCodeSymbols_fpu32.lib这个库。
总之感觉这个CSM的用户体验贼瞎,一直用来挺顺,最后走个坑 - -
非常感謝你的解答!
我目前只設置的PSWD 2/3,未設置PSWD 0/1,這樣芯片可以加密,但不會使能ECSL,仿真器可以連接。連接仿真器后,看到DcsmZ1Regs和DcsmZ2Regs如下圖所示,應該是已經加密。加密后如果不解密,應該是不能擦除和燒寫程序的,但是我測試了一下,不執行解密動作依舊可以擦除燒寫(加密的程序DCSM_Z1_ZoneSelectBlock.asm和DCSM_Z2_ZoneSelectBlock.asm已配置,而新燒寫的程序未配置,保持controlsuite中的初始狀態。注:如果新燒寫的程序配置.asm的話,可以擦除但無法正常燒寫)。請問你有遇到這樣的情況嗎?謝謝!
你好!我在将28377D双核加密后,无法再利用API对程序进行擦除和更新了(API程序和应用程序都分配给了同一个加密zone)。加密之前,是OK的。
以CPU1的程序更新为例,目前我将所有的Flash和RAM(D0/D1 LSxRAM)都分配给了zone1,在进行程序擦除和烧写前,先通过(IpcRegs.PUMPREQUEST.all = IPC_PUMP_KEY | 0x2;)让CPU1获取Flash pump,然后再通过( DcsmCommonRegs.FLSEM.bit.KEY = 0xA5;DcsmCommonRegs.FLSEM.bit.SEM = 0x01;)让zone1获取Flash pump。但是这样依旧不能正常的擦除和更新程序。
请问你有没有遇到这样的问题呢?谢谢!
这就不清楚了,全是FF应该是可以写OTP的,更新个CCS版本试试。你上个回帖的界面,不是在那个界面刷的。那个只是设置DEBUG时寄存器的相关值。应该是在连接目标板之后,MEMORY MAP里的一个ON CHIP FLASH里面刷的。