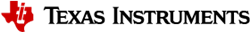工具/软件:
我想使用 keystore _PSA_importKey、因此我们根据示例代码实现它并检查其运行情况。
我发现代码进入了 exception_handlerSpin 的无限循环。
我怀疑 PSA_import_key () 在内部用于 keystore PSA_importKey。
要检查 PSA_IMPORT_KEY () 的操作、
我创建了以下代码 ①、并使用与示例代码相同的参数检查了其操作。
然后、我们收到错误“PSA_ERROR_INVALID_PARAMUST"。“。
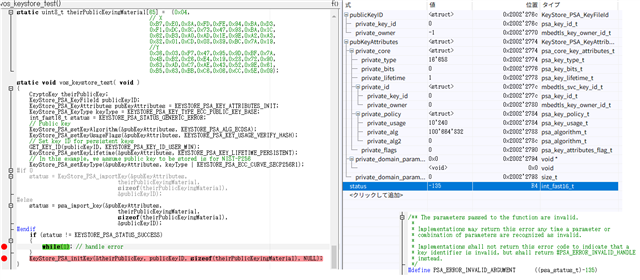
我还创建并运行了代码 ②、但返回了“PSA_ERROR_INSUFFICIENT_MEMOR"。“。
您能解释一下为什么这些错误代码是由 PSA_IMPORT_KEY () 报告的吗?
此外,当使用 keystore _PSA_importKey() 时,它会进入一个无限的 Exception_handlerSpin 循环。 是否有办法解决此问题?
--
① μ s
simplelink_lowpower_f3_SDK_9_10_00_83\source\ti\drivers\ECDSA.h
当我模拟示例代码运行以下源代码时、状态值为–135(传递给函数的参数无效。)
*当使用 keystorage_PSA_importKey 时, exception_handlerSpin 函数进入一个无限循环。
static uint8_t theirPublicKeyingMaterial[65] = {0x04,
// X
0xB7,0xE0,0x8A,0xFD,0xFE,0x94,0xBA,0xD3,
0xF1,0xDC,0x8C,0x73,0x47,0x98,0xBA,0x1C,
0x62,0xB3,0xA0,0xAD,0x1E,0x9E,0xA2,0xA3,
0x82,0x01,0xCD,0x08,0x89,0xBC,0x7A,0x19,
//Y
0x36,0x03,0xF7,0x47,0x95,0x9D,0xBF,0x7A,
0x4B,0xB2,0x26,0xE4,0x19,0x28,0x72,0x90,
0x63,0xAD,0xC7,0xAE,0x43,0x52,0x9E,0x61,
0xB5,0x63,0xBB,0xC6,0x06,0xCC,0x5E,0x09};
static void vos_keystore_test( void )
{
CryptoKey theirPublicKey;
KeyStore_PSA_KeyFileId publicKeyID;
KeyStore_PSA_KeyAttributes pubKeyAttributes = KEYSTORE_PSA_KEY_ATTRIBUTES_INIT;
KeyStore_PSA_KeyType keyType = KEYSTORE_PSA_KEY_TYPE_ECC_PUBLIC_KEY_BASE;
int_fast16_t status = KEYSTORE_PSA_STATUS_GENERIC_ERROR;
// Public key
KeyStore_PSA_setKeyAlgorithm(&pubKeyAttributes, KEYSTORE_PSA_ALG_ECDSA);
KeyStore_PSA_setKeyUsageFlags(&pubKeyAttributes, KEYSTORE_PSA_KEY_USAGE_VERIFY_HASH);
// Set key ID for persistent keys
GET_KEY_ID(publicKeyID, KEYSTORE_PSA_KEY_ID_USER_MIN);
KeyStore_PSA_setKeyLifetime(&pubKeyAttributes, KEYSTORE_PSA_KEY_LIFETIME_PERSISTENT);
// In this example, we assume public key to be stored is for NIST-P256
KeyStore_PSA_setKeyType(&pubKeyAttributes, keyType | KEYSTORE_PSA_ECC_CURVE_SECP256R1);
#if 0
status = KeyStore_PSA_importKey(&pubKeyAttributes,
theirPublicKeyingMaterial,
sizeof(theirPublicKeyingMaterial),
&publicKeyID);
#else
status = psa_import_key(&pubKeyAttributes,
theirPublicKeyingMaterial,
sizeof(theirPublicKeyingMaterial),
&publicKeyID);
#endif
if (status != KEYSTORE_PSA_STATUS_SUCCESS)
{
while(1); // handle error
}
KeyStore_PSA_initKey(&theirPublicKey, publicKeyID, sizeof(theirPublicKeyingMaterial), NULL);
}
② μ s
simplelink_lowpower_f3_SDK_9_10_00_83\source\ti\drivers\cryptoutils\cryptokey\CryptoKeyKeyStore_PSA.h
当我模拟示例代码运行以下源代码时、状态值将为–141(没有足够的运行时内存)。
*当使用 keystorage_PSA_importKey 时, exception_handlerSpin 函数进入一个无限循环。
static uint8_t keyingMaterial[16] = {0x1f, 0x8e, 0x49, 0x73, 0x95, 0x3f, 0x3f, 0xb0,
0xbd, 0x6b, 0x16, 0x66, 0x2e, 0x9a, 0x3c, 0x17};
static void vos_keystore_test( void )
{
CryptoKey cryptoKey;
KeyStore_PSA_KeyFileId keyID;
int_fast16_t status;
KeyStore_PSA_KeyAttributes attributes = KEYSTORE_PSA_KEY_ATTRIBUTES_INIT;
// Assign key attributes
KeyStore_PSA_setKeyUsageFlags(&attributes, (KEYSTORE_PSA_KEY_USAGE_DECRYPT | KEYSTORE_PSA_KEY_USAGE_ENCRYPT));
KeyStore_PSA_setKeyAlgorithm(&attributes, KEYSTORE_PSA_ALG_CCM);
KeyStore_PSA_setKeyType(&attributes, KEYSTORE_PSA_KEY_TYPE_AES);
KeyStore_PSA_setKeyLifetime(&attributes, KEYSTORE_PSA_KEY_LIFETIME_PERSISTENT);
// Set key ID
GET_KEY_ID(keyID, KEYSTORE_PSA_KEY_ID_USER_MIN);
KeyStore_PSA_setKeyId(&attributes, keyID);
// Import the keyingMaterial
#if 0
status = KeyStore_PSA_importKey(&attributes,
keyingMaterial,
sizeof(keyingMaterial),
&keyID);
#else
status = psa_import_key(&attributes,
keyingMaterial,
sizeof(keyingMaterial),
&keyID);
#endif
if (status != KEYSTORE_PSA_STATUS_SUCCESS)
{
while(1); // handle error
}
KeyStore_PSA_initKey(&cryptoKey, keyID, sizeof(keyingMaterial), NULL);
}
——