Part Number: TDA4AL-Q1
hi TI experts:
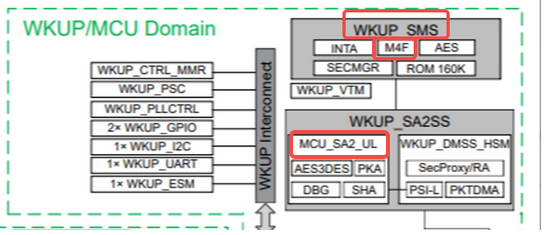
Based on the TDA4AL platform, how do I want to implement vHSM based key and certificate storage and call MCU based on WKUP SMS M4F_ SA2_ UL implements functions such as accelerated decryption
This thread has been locked.
If you have a related question, please click the "Ask a related question" button in the top right corner. The newly created question will be automatically linked to this question.
Part Number: TDA4AL-Q1
hi TI experts:
Based on the TDA4AL platform, how do I want to implement vHSM based key and certificate storage and call MCU based on WKUP SMS M4F_ SA2_ UL implements functions such as accelerated decryption

已咨询e2e产品线工程师,因为这周感恩节美国放假,所以回复会慢些,请关注下面帖子的回复。
https://e2e.ti.com/support/processors-group/processors/f/processors-forum/1295789/tda4al-q1-what-is-the-actual-range-between-the-key-and-certificate
Hi shine:
The problem summary is as follows:
Question 1: TDA4AL has the WKUP SMS M4F core, which can support third-party Vertor HSM software packages. However, TDA4AL does not have a built-in HSM security chip. Therefore, if the certificate and public key passed by OEM have efuse intervals in EMMC, there is a problem. The problem is that efuse is readable, so the confidentiality of the key and certificate cannot be guaranteed? Or you may have a better recommended solution here
Question 2: If the certificate and key are stored in efuse, what is the current efuse space size of the TDA4AL board? Here, I can evaluate whether efuse memory is sufficient.