“线程”中讨论的其它部件:TMS320F280039C
尊敬的专家:
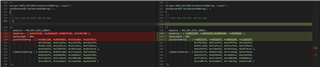
我使用相同的设置条件来验证网络工具和 MCU 加密的输出是否相同。
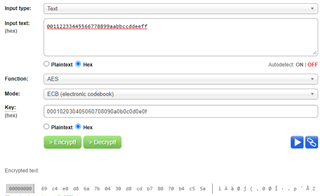
模式设置:AES 128位加密用于 ECB 模式。
Web 工具 URL:aes.online-domain-tools.com
MCU:TMS320F280039C 和 TI 示例代码(AES_ex1_ECB)
为什么微控制器 AES 模块的加密与在线工具的输出不同?
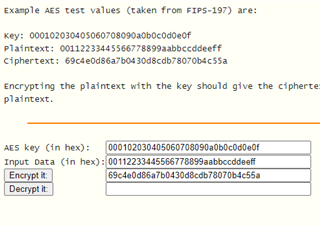
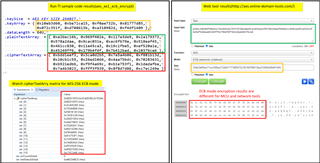
网络加密工具的加密输出如下:
输入数据:{0x00112233,0x44556677,0x8899aabb,0xccddeeff}
密钥 :{0x00010203,0x04050607,0x08090a0b,0x0c0d0e0f}
CYPHER:{0x69c4e0d8,0x6a7b0430,0xd8cdb780,0x70b4c55a}
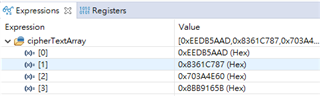
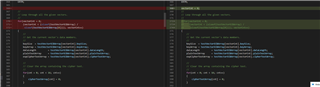
MCU TMS320F280039C 输出加密的结果如下:
输入数据:{0x00112233,0x44556677,0x8899aabb,0xccddeeff}
密钥:{0x00010203,0x04050607,0x08090a0b,0x0c0d0e0f}
CYPHER:{0xEEDB5AAD,0x8361C787,0x703A4E60,0x8BB9165B}
感谢你的帮助。